Internet of Things (IOT) is the technology that allows us to transmit data from and commands to smart devices in real-time. IoT is a network of devices connected via the Internet, with a hub that can analyze the aggregated data. The IoT endpoints can be a person, an animal, a home, a farm, a building, or a whole city. But in all cases these things “talk” to each other without any human intervention via an IoT protocol.
There are different protocols for the different layers in an IoT architecture and in this paper we take a look at just a few of them, include: MQTT, HTTP and CoAP.
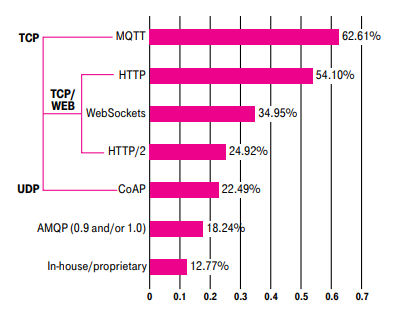
Popularity of IoT data transport protocol in 2018 (Source: t-mobile.com)
1. Message Queuing Telemetry Transport (MQTT)
What is MQTT?
MQTT is a machine to machine internet of things connectivity protocol.

The world of M2M (Machine to Machine)
It is a publish and subscribe system where we can publish and receive the messages as a client. It makes it easy for communication between multiple devices.
It is a simple messaging protocol designed for the constrained devices and with low bandwidth, so it’s a perfect solution for the internet of things applications.
It is an extremely lightweight and publish-subscribe messaging transport protocol. It is useful for the connection with the remote location where the bandwidth is a premium. These characteristics make it useful in various situations, including constant environments such as for communication machine to machine and internet of things contexts.
Characteristics of MQTT
The MQTT has some unique features which are hardly found in other protocols. Some of the features of an MQTT are given below:
- It does not require that both the client and the server establish a connection at the same time.
- It allows the clients to subscribe to the narrow selection of topics so that they can receive the information they are looking for.
- It provides faster data transmission, like how WhatsApp/messenger provides a faster delivery. It’s a real-time messaging protocol.
- It is designed as a simple and lightweight messaging protocol that uses a publish/subscribe system to exchange the information between the client and the server.
- It is a machine to machine protocol, it provides communication between the devices.
MQTT Architecture
To understand the MQTT architecture, we first look at the components of the MQTT: message, client, server and topic.
Message
The message is the data that is carried out by the protocol across the network for the application. When the message is transmitted over the network, then the message contains the following parameters:
- Payload data
- Quality of Service (QoS)
- Collection of Properties
- Topic Name
Client
In MQTT, the subscriber and publisher are the two roles of a client. The clients subscribe to the topics to publish and receive messages. In simple words, we can say that if any program or device uses an MQTT, then that device is referred to as a client. A device is a client if it opens the network connection to the server, publishes messages that other clients want to see, subscribes to the messages that it is interested in receiving, unsubscribes to the messages that it is not interested in receiving, and closes the network connection to the server.
In MQTT, the client performs two operations:
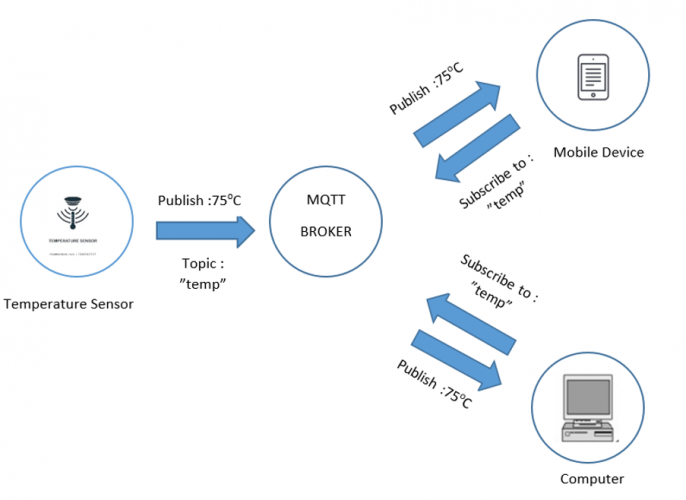
Example illustrating data retrieval and transmission (temperature) in MQTT
Publish: When the client sends the data to the server, then we call this operation as a publish.
Subscribe: When the client receives the data from the server, then we call this operation a subscription.
Server
The device or a program that allows the client to publish the messages and subscribe to the messages. A server accepts the network connection from the client, accepts the messages from the client, processes the subscribe and unsubscribe requests, forwards the application messages to the client, and closes the network connection from the client.
Topic
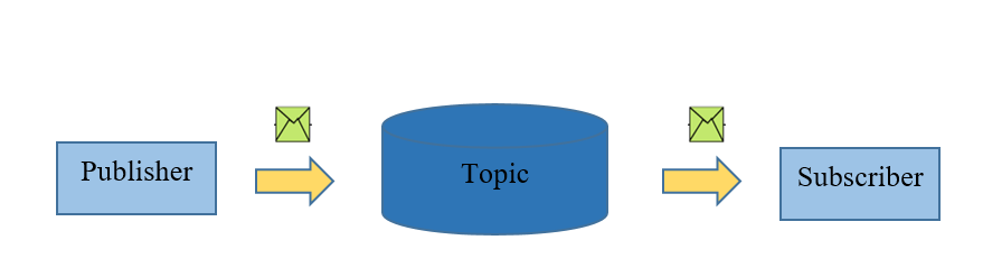
The name of the Topic
The label provided to the message is checked against the subscription known by the server is known as TOPIC.
MQTT Applications
Facebook currently uses MQTT for its Messenger app, not only because the protocol conserves battery power during mobile phone-to-phone messaging, but also because the protocol enables messages to be delivered efficiently in milliseconds (ms), despite inconsistent internet connections across the globe.
Most major cloud services providers, including Amazon Web Services (AWS), Google Cloud, IBM Cloud and Microsoft Azure, support MQTT.
MQTT is well suited to applications using M2M and IoT devices for purposes such as real-time analytics, preventative maintenance and monitoring in environments, including smart homes, healthcare, logistics, industry and manufacturing
Advantages and disadvantages of MQTT protocol
Advantages of MQTT protocol:
- Efficient data transmission and quick to implement due to its being a lightweight protocol;
- Low network usage, due to minimize data packets;
- Efficient distribution of data;
- Successful implementation of remote sensing and control;
- Fast and efficient message delivery;
- Usage of small amounts of power, which is good for the connected devices;
- Reduction of network bandwidth
Disadvantages of MQTT protocol:
- MQTT has slower transmit cycles compared to CoAP.
- MQTT’s resource discovery works on flexible topic subscription, whereas CoAP uses a stable resource discovery system.
- MQTT is unencrypted. Instead, it uses TLS (Transport Layer Security)/SSL (Secure Sockets Layer) for security encryption.
- It is difficult to create a globally scalable MQTT network.
2. Hypertext Transfer Protocol (HTTP)
What is HTTP?
HTTP stands for Hypertext Transfer Protocol, an application protocol for distributed, collaborative, hypermedia information systems that allows users to communicate data on the World Wide Web
Example: http://www………: URL beginning with HTTP scheme
To be more specific, HTTP is a stateless request/response protocol where clients request information from a server and the server responds to these requests accordingly (each request is independent of the other). It allows the fetching of resources, such as HTML document
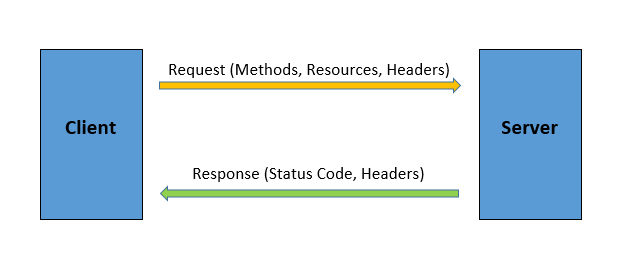
HTTP request/response pattern
What is the purpose of HTTP?
HTTP was invented alongside HTML to create the first interactive, text-based web browser: the original World Wide Web. Today, the protocol remains one of the primary means of using the Internet.
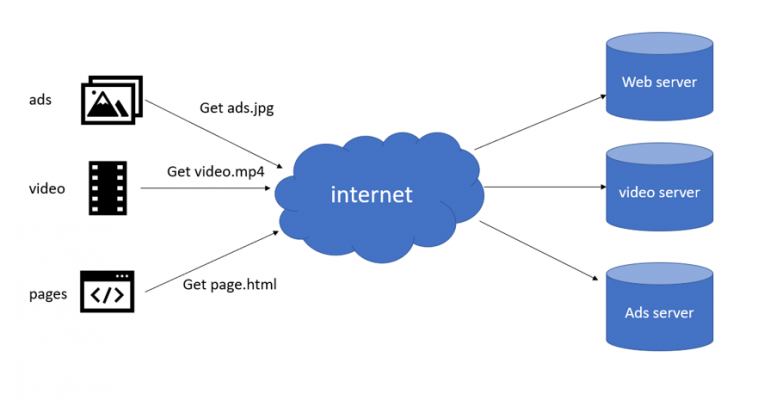
Data through the internet
How does HTTP work?
HTTP data rides above the TCP protocol, which guarantees reliability of delivery, and breaks down large data requests and responses into network-manageable chunks.
This is how it works: at first, clients send a SYN packet to the server and then the web server will respond with SYN-ACK packet to confirm success of receiving. After which, the client again sends a ACK packet, concluding a connection establishment – this is also commonly referred to as a 3-way handshake. In addition, the client sends a HTTP request to the server for a resource and waits for it to respond to a request. Then the web server will process the request, find the resource and send the response to the client. If no more resources are required by the client, it sends a FIN packet to close the TCP connection.
HTTP Applications
HTTP protocol is used for bootstrap the World Wide Web to transmit data in the form of text, audio, images, and video from the Web Server to the user’s web browser and vice versa. HTTP is currently the data transmission platform of today’s web browsing application and is widely used in Internet of Things systems. Even though Http protocol has many disadvantages in transmitting data and is not as suitable as those proficient protocols such as MQTT, CoAP, AMQP using for IoT, this protocol is still popular in smart-home industry as well as many advanced microcontrollers and microprocessor. For example, systems which are based on the new generation of raspberry pi use http protocol to transmit data. Arduino also uses this protocol to communicate with other devices. Besides, there are 3 more new versions of http which have manifested in order to compensate for the downsides of the old one and to be applied for particular situations.
Advantages and disadvantages of HTTP
Advantages of applying HTTP:
- Search capabilities: Although HTTP is a simple messaging protocol, it includes the ability to search a database with a single request. This allows the protocol to be used to carry out SQL searches and return results conveniently formatted in an HTML document.
- Ease of programming: HTTP is coded in plain text and therefore is easier to follow and implement than protocols that make use of codes that require lookups. Data is formatted in lines of text and not as strings of variables or fields.
- Security: HTTP 1.0 downloads each file over an independent connection and then closes the connection. So this reduces the risk of interception during transmission significantly
Disadvantages of applying HTTP protocol:
- Not suitable for small devices: As small devices, such as wireless sensor, do not require much interaction and they consume very little power, HTTP is too heavy to be a good fit for these devices. An HTTP request requires a minimum of nine TCP packets, even more when you consider packet loss from poor connectivity, and plain text headers can get very verbose.
- Not designed for event-based communication: Most of the IOT applications are event based. The sensor devices measure for some variable like temperature, air quality and might need to take event driven decisions like turning off a switch HTTP was designed for a request-response based communication rather than an event-driven communication. Also, programming this event based systems using HTTP protocol becomes a big challenge especially because of the limited computing resources on the sensor devices.
- Real-time problem: After requesting a resource to the server, the client has to wait for the server to respond, leading to slow transfer of data. IOT sensors are small devices with very limited computing resources and hence cannot work efficiently in a synchronous manner. All the widely used IOT protocols are based on asynchronous models.
3. Constrained Application Protocol (CoAP)
What is CoAP?
CoAP is a simple protocol with low overhead specifically designed for constrained devices (such as microcontrollers) and constrained networks. This protocol is used in M2M data exchange and is very similar to HTTP, even if there are important differences that we will discuss later.
CoAP has the following main features:
- Constrained web protocol fulfilling M2M requirements.
- Security binding to Datagram Transport Layer Security (DTLS).
- Asynchronous message exchanges.
- Low header overhead and parsing complexity.
- URI and Content-type support.
- Simple proxy and caching capabilities.
- Optional resource discovery.
- UDP (User Datagram Protocol) binding with optional reliability supporting unicast and multicast requests.
CoAP Structure Model
CoAP interactive model is similar to HTTP’s client/server model. CoAP employs a two layers structure. The bottom layer is a message layer that has been designed to deal with UDP and asynchronous switching. The request/response layer concerns communication methods and deals with request/response messages.
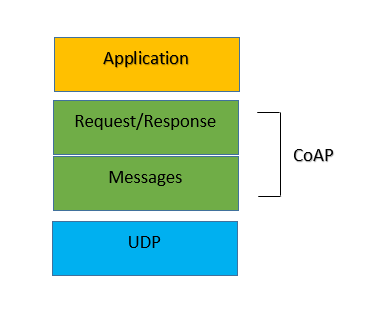
Abstract Layer of CoAP
CoAP Messages Model
Message Layer supports 4 types of messages: CON (Confirmable), NON (Non-confirmable), ACK (Acknowledgement), RST (Reset).
Reliable message transport: A CON message is retransmitted until the recipient sends an ACK message with the same message ID. Using default timeout and decreasing counting time exponentially when transmitting a CON message. If a recipient is not able to process a message, it responses by replacing ACK message with RST message.
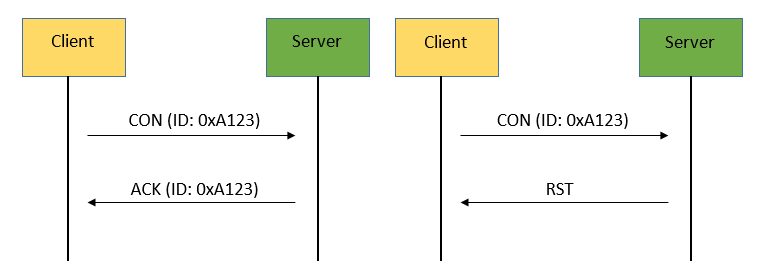
Reliable message delivery
Unreliable message transport: A message that does not require reliable delivery, can be sent as a NON message. These are not acknowledged, but still have a message ID for duplicate detection. Figure 3 shows unreliable message transport.
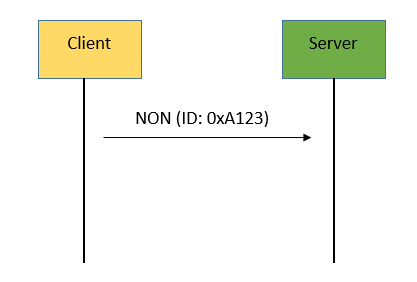
Unreliable message delivery
CoAP Request/Response Model
Piggy-backed: The request is sent using CON or NON message, and if immediately available, the response to a request carried in a CON message is carried in the resulting ACK message. For successful response, ACK contains response messages (identified by using a token), for failure response, ACK contains failure response code.
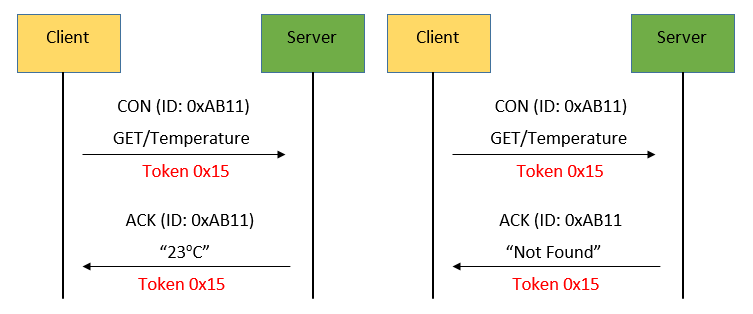
Two GET requests with immediate responses, one successful, one not found
Separate response: If a server receives a CON message type message but is not able to respond to this request immediately, it will send an empty ACK message in case the client resends this message. When the server is ready to respond to this request, it will send a new CON message to client and client reply a CON message with acknowledgment. The ACK message from the client is just to confirm the CON message from the server.
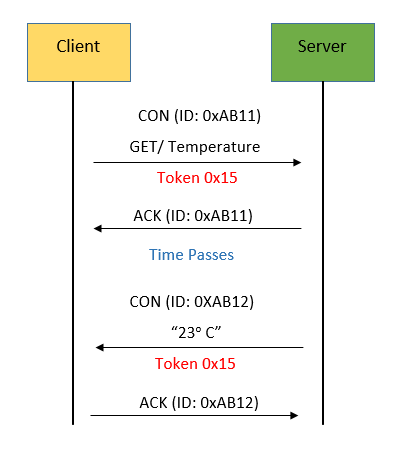
A GET request with a separate response
Advantages and Disadvantages of CoAP
Advantages of CoAP protocol
- It is a simple protocol and uses less overhead due to operation over UDP. It allows short wake up times and long sleepy states. This helps in achieving long battery life for use in
- It uses IPSEC (IP Security) or DTLS (Datagram Transport Layer Security) to provide secure communication.
- Synchronous communication is not necessary in CoAP protocol.
- It has lower latency compared to HTTP.
- It avoids unnecessary retransmissions so that it consumes less power than HTTP.
- CoAP protocol is used as the best protocol choice for home communication networks. It is used in information appliances, communication equipment and control equipment in smart home networks.
Disadvantages of CoAP protocol
- CoAP is an unreliable protocol due to the use of UDP. Hence CoAP messages reach unordered or will get lost when they arrive at destination
- It acknowledges each receipt of the message and hence increases processing time. Moreover, it does not verify whether the received message has been decoded properly or not.
- It is an unencrypted protocol like MQTT and uses DTLS to provide security at the cost of implementation overhead.
- CoAP has communication issues for devices behind NAT (Network Address Translation).
CoAP Application for Smart Homes
Information appliance, control equipment and communication equipment in Smart home networks have the characters of low-cost and lightweight. Thus, CoAP could be seen as the best protocol choice for home communication networks.
Smart home network provides controlling and monitoring energy of home devices. Energy control systems employ smart socket management and monitor power consuming equipment to provide voltage, current and other energy information. It could realize accident warning, remote control and dynamic energy saving. Every data collection node with a CoAP client could exchange information with other nodes. CoAP could both be installed in LAN or Internet. Unlike many wireless protocols for home automotive devices, CoAP is designed not constrained in a local network but provides the fundamental basis of the web.
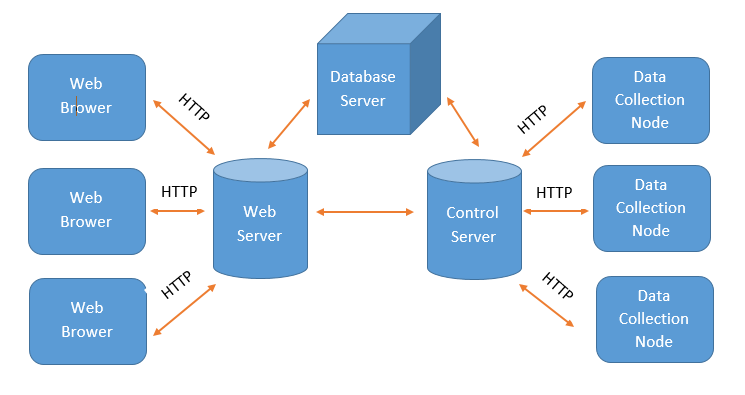
Energy control system
In system networking, data collection nodes consist of one proxy, smart socket and wireless data collection module. Energy information and environment information of equipment is collected by the smart socket and transported to a data collection module through wireless channel, then sent serial data to proxy to process and pack data. Control server analyzes all the data and stores it in a database. The system integrates home network and Internet, users can access the system webpage to remotely control switches, manage configuration, query energy consumption, etc.
Summary
| Criteria | MQTT | HTTP | CoAP |
| Year | 1999 | 1997 | 2010 |
| Form | Message Queue Telemetry Transport | Hypertext Transfer Protocol | Constrained Application Protocol |
| Architecture | Client/Broker | Client/Server | Client/Server |
| Pattern | Publish/Subscribe | Request/Response | Request/Response |
| Header Size | 2 Byte | Undefined | 4 Byte |
| Message Size | Small and Undefined (up to 256 MB maximum size) | Large and Undefined (depends on the web server) | Small and Undefined (normally small to fit in single IP datagram) |
| Semantics/Methods | Connect, Disconnect, Publish, Subscribe, Unsubscribe, Close | Get, Post, Head, Put, Patch, Options, Connect, Delete | Get, Post, Put, Delete |
| Cache and Proxy Support | Partial | Yes | Yes |
| Quality of Services (QoS)/Reliability | QoS 0 – At most once
(Fire and Forget) QoS 1 – At least once QoS 2 – Exactly once |
Limited (via Transport Protocol – TCP) | Confirmable Message (similar to At most once) or Non-confirmable (similar to At least once) |
| Transport Protocol | TCP | TCP | UDP, (Stream Control Transmission Protocol)
|
| Security | TLS /SSL | TLS/SSL | DTLS , IPsec |
| Default Port | 1883/8883 (TLS/SSL) | 80/443 (TLS/SSL) | 5683 (UDP Port) |
| Encoding Format | Binary | Text | Binary |
| Licensing Model | Open Source | Free | Open Source |
| Organizational Support | IBM, Facebook, Eurotech, Cisco, Red Hat, Software AG, Tibco, ITSO, M2Mi, Amazon Web Services (AWS), InduSoft, Fiorano | Global Web Protocol Standard | Large Web Community Support, Cisco, Contiki, Erika, IoTivity |
Conclusion
In general, there are numerous different IoT protocols that support the Internet of Things and HTTP, MQTT, CoAP are the three main dominant protocols in the IOT market nowadays because of its superb benefits which we have already discussed above. However, it is noticeable that while HTTP protocol is suitable for web browsing application, the other two are more fitting in the IoT purposes such as real-time communication, preventative maintenance and monitoring in environments, including smart homes and manufacturing industry.
Overall, what is really important in applying IoT technique is the awareness of the business’s requirements as well as the advantages and drawbacks of the protocols offered by the market, and the ability to choose to best suit specific cases. Thanks for reading this article. If you have any question, feel free to contact us at email: info@daviteq.com


 Tiếng Việt
Tiếng Việt